
Overview
In modern enterprise environments, Windows Update management via Microsoft Intune (MDM) is a cornerstone of system compliance and security. However, a recurring issue was observed where devices failed to install updates, despite being correctly enrolled and configured. This article outlines the diagnostic process, technical interventions, and the underlying cause—linked to KB4023057—based on internal troubleshooting and external validation.
Symptomatology
Affected devices exhibited the following behaviors:
- No updates were detected or installed, even though they were outdated.
- The “Check for updates” button appeared disabled but remained functional.
- Devices showed inconsistent update behavior depending on their provisioning status (new vs. existing).

Digging deeper
It appears that something has been mixed up with the update policies.
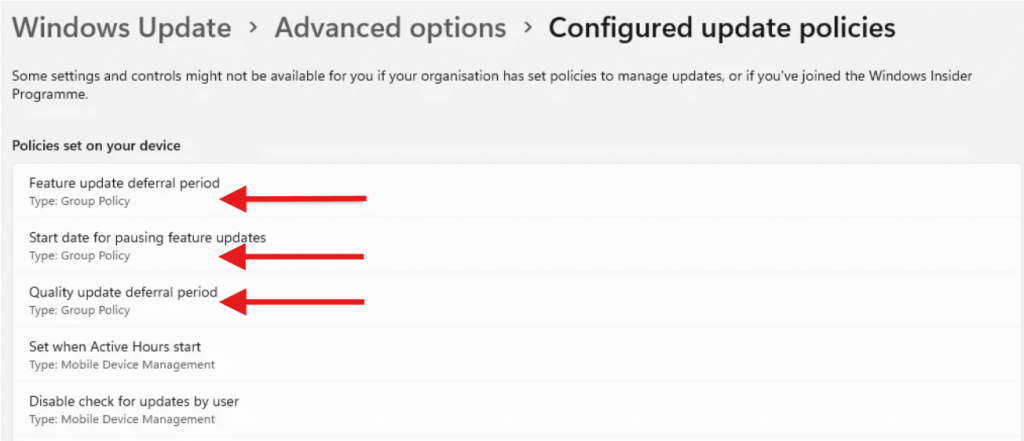
On a cloud-only Intune-managed device, only “Mobile Device Management” type policies should be present.
However, checking the advanced update options, there seem to be some Group Policy (GPO) settings still active on these devices.
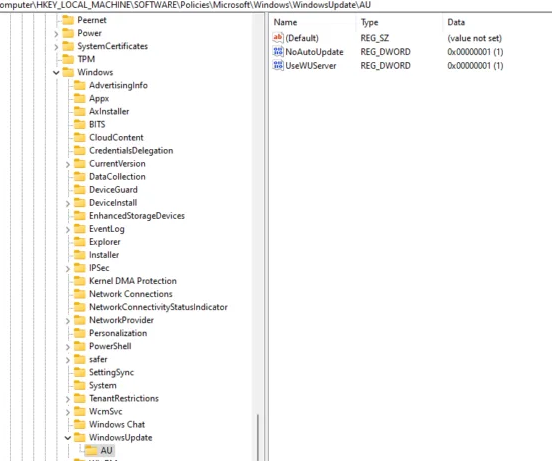
Also the registry hive: HKLM:SOFTWAREPoliciesMicrosoftWindowsWindowsUpdate
Which, as far as I know, is only populated when using group policies, seems to be in use. The registry key “NotAutoUpdate” set to “1” looks highly suspicious to me.
So, I decided to manually delete the registry hive for testing purposes — and Windows Update immediately reacted by automatically looking for pending updates.
Unfortunately, removing the hive does not immediately resolve the issue on all devices. It appears that the Group Policies are also cached in the path HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsUpdateUpdatePolicyGPCache. Only after this cache is cleared Windows kindly began searching for updates again.
The Fix
Deploying an Intune remediation (thanks to everything365.online) resolved the issue in our environment.
Tipp: A detection script can also be executed as a standalone component for reporting purposes.
The detection script reported that nearly the whole environment was not installing the latest updates caused by the registry keys.
The Detection script contained the following code:
#Variable decleration
$scriptname = 'PR_CMP_WindowsUpdateFix_Detection_001'
$logfile = "C:\Programdata\Script_Logs\$ScriptName.log"
#Start logging
Write-Host "$scriptname - "
Start-Transcript -path $logfile -Force -Append
Write-Host "################################### Start script: $ScriptName ###################################"
$gpoRegistryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate"
# Check if the Group Policy registry key exists
if (Test-Path $gpoRegistryPath) {
Write-Output "Registry key exists."
exit 1
}
else {
Write-Output "Registry key does not exist."
exit 0
}
#End logging
Write-Host "#################################### End script: $ScriptName ####################################"
Stop-TranscriptThe remediation script removes both the “GPO” and “MDM” registry keys and then triggers an MDM sync to retrieve the latest policy settings.
The Remediation script:
#Variable decleration
$scriptname = 'PR_CMP_WindowsUpdateFix_Remediation_001'
$logfile = "C:\Programdata\Script_Logs\$ScriptName.log"
#Start logging
Write-Host "$scriptname - "
Start-Transcript -path $logfile -Force -Append
Write-Host "################################### Start script: $ScriptName ###################################"
# Define the registry paths
$gpoRegistryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate"
$mdmRegistryPath = "HKLM:\SOFTWARE\Microsoft\WindowsUpdate\UpdatePolicy"
try {
# Check and remove Group Policy registry key (if it exists)
if (Test-Path $gpoRegistryPath) {
Remove-Item -Path $gpoRegistryPath -Recurse -Force
Write-Output "Group Policy registry key deleted."
} else {
Write-Output "Group Policy registry key does not exist, no action taken."
}
# Check and remove MDM Update Policy registry key (if it exists)
if (Test-Path $mdmRegistryPath) {
Remove-Item -Path $mdmRegistryPath -Recurse -Force
Write-Output "MDM Update Policy registry key deleted."
} else {
Write-Output "MDM Update Policy registry key does not exist, no action taken."
}
# Start MDM Sync after registry keys are removed
try {
[Windows.Management.MdmSessionManager, Windows.Management, ContentType = WindowsRuntime]
$session = [Windows.Management.MdmSessionManager]::TryCreateSession()
$session.StartAsync() | Out-Null
Write-Output "MDM sync initiated."
}
catch {
Write-Output "Failed to initiate MDM sync: $($_.Exception.Message)"
}
# Exit with 0 to indicate successful remediation
exit 0
}
catch {
# If an error occurs, output the error message and exit with 1 to indicate failure
Write-Output "Failed to delete the registry key(s): $($_.Exception.Message)"
exit 1
}
#End logging
Write-Host "#################################### End script: $ScriptName ####################################"
Stop-TranscriptBy now — approximately three months and several additional devices in the field later — the issue appears to be permanently resolved.
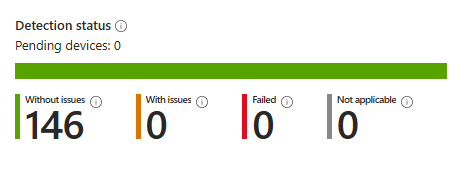
After discovering this issue and finding a simple workaround, I started looking into whether others were experiencing similar problems with Windows Update deployments — surely, we couldn’t be the only ones.
In doing so, I came across a few articles that identified KB4023057 as the potential cause of the problem — though, of course, I can’t personally confirm this. Just for the record!

Schreibe einen Kommentar